Article snapshot
- As devices become more connected and processes more digitised, mining companies will need to contend with an increased number of network born security threats
- IT and operational technology (OT) integration, combined with other cyber security risk factors, mean mining business leaders will need to take a holistic view of their organisations, including challenges arising from digital silos
- Telstra’s Cyber Security 2016 report found that only 22 per cent of companies are ready for the risks involved in cloud-based service adoption, indicating that there is room for improvement in cyber security planning
- There has been a significant shift in responsibly of cyber security to the C-level – implying that cyber security has moved from being merely an IT consideration to becoming a business focus
- In 2014, the scope of IT security budgets was one of the biggest challenges in combating cyber security breaches. In 2016, the biggest challenge is finding talent with the necessary security skills
- Alongside the need for tactical skills, companies must foster a culture of awareness throughout their organisations, not just at the board level
- Meeting the rising number of cyber security challenges may seem daunting for in-house IT departments with limited budgets and skills , but partnering can raise defensive capabilities
Mining is undergoing the most significant change since the introduction of modern industrial equipment. The convergence of IT and operational technology through industrial automation, the uptake of smart devices for real-time operations management and remote operations, and the adoption of cloud-based services is driving significant change, creating a data-driven industry.
The connected mine site and its supply chain must now ensure operations data is kept secure to prevent business disruption and provide a platform for innovation.
Like most industries, mining needs to approach cyber security as a whole-of-business risk and not just an IT risk. By using the right combination of people, processes and technology, mining companies can then reap the full benefits of the digital world.
Organisations that attribute security responsibility to C-level or business line managers and conduct frequent cyber security briefings are better placed to handle security incidents, Telstra’s Cyber Security Report 2016 states. Amid an escalating number of security threats, mining companies must focus on protecting critical assets to maintain business continuity, and strategies for responding to an attack are becoming as important as those geared towards prevention.
Growing cyber security challenges
Information technology is creating a new era of process optimisation and business innovation for the resources sector. As more and more equipment and software becomes connected to private and public data networks, the potential – no matter how small – for a security breach is increasing.
The range of cyber security threats is also increasing, with almost daily incidents of malicious hacking, ransomware, data leaks, theft and electronic fraud occurring globally. The Telstra Cyber Security Report 2016 found a marked increase in business-interrupting security breaches during an average month – more than twice what was reported in 2014.
In the mining and resources sector, the study found that only 22 per cent of companies are ready for the risks involved in cloud-based service adoption, indicating a lot of room for improvement in cyber security planning. This needs to become an integral part of project design, rather than something retrofitted as an afterthought.
Neil Campbell, Director of Security at Telstra, says there are a number of important findings from the report that can benefit mining companies. These include looking at readiness, evolving threats and trends, and how businesses respond to security incidents.
“Regarding readiness and maturity, last year there was a significant shift in responsibility at the C-level which involved regular briefings from IT security staff to senior managers. This strongly implies that cyber security has moved from merely being an IT consideration to becoming a business focus. This higher priority is due to a greater awareness of the disruption breaches cause,” Campbell says.
Another significant trend over the past two years since the report was last published, has been a rise in malicious phishing attacks for malware delivery. Phishing is now the main vehicle for malware distribution and the type that stood out last year was ransomware.
“As much as 60 per cent of the CryptoLocker attack instances reported in the study were detected in Australia. These were previously spam and phishing attacks and considered a nuisance. Criminals are now getting financial outcomes based on an attack,” Campbell says, adding ransomware instances will continue to increase this year and “we are only seeing the tip of the iceberg”.
|
Volume and frequency of attacks increasing Mining industry executives need to be aware of significant increases in the size and frequency of attacks, with a lot more activity being detected across all industries. Telstra’s Campbell says that, as the threat landscape grows, a lot more is being detected “by default”. Hackers today are more likely to perform short, more frequent attacks rather than attempt big, longer campaigns. “They can do more damage that way and gain more access when the business doesn’t know when the next attack is coming,” he says.
|
Alan Hindes, Global Industry Executive, Mining, Oil and Gas at Telstra says mining companies are facing more security challenges due to the move to centralising operations and a greater impact of the Internet of Things (IoT).
“Security budgets were a big issue 18 months ago, but now the challenge is finding talent with the necessary security skills,” Hindes says. “The industry needs to continue to invest and is challenged as the use of smart devices and real-time information put more emphasis on data protection and cyber security.”
The Telstra Cyber Security Report 2016 confirmed the shift in recognition at the board and C-level around the entire cyber security environment – from protecting the company image to protecting data.
“The mining industry was suffering from a high number of attacks,” Hindes says. “Like the banking sector, as more devices come onto the network across a mine there is greater vulnerability, and as companies use more cloud-based services to keep capital costs down, there is an inevitable trade-off between efficiencies and security challenges.”
No company surveyed in Telstra’s research had escaped some form of cyber-attack and the sophistication of these breaches has grown beyond simple phishing. And despite the increase in security activity, the “restoration time”, or time from recognition of an attack to remediation, was about average in mining.
Evolving laws keep privacy and access top of mind
In addition to the operational aspects of cyber security like malware attacks, mining companies now carry a greater burden complying with local and international laws governing the storage and processing of sensitive information – from customer details to supplier and government contracts.
“There are ongoing updates to the Privacy Act regarding the use of personal details and organisations must be competent enough to handle this information in a reasonable way,”
Campbell says. “When it comes to sharing intellectual property with third parties they need to have visibility over how data is used, who is looking at it, and what to do when an incident occurs.
According to Hindes, there are continuous challenges with access to certain systems because of the way resource companies work with partners. “Who is accessing which databases? A good start to meeting regulatory compliance is to make sure that your partners adopt the same level of security that you require,” he says.
Governance and compliance is also becoming more complex in an increasingly global supply chain. Multi-national mining companies have WANs (wide area network) that cover the world, which has huge implications for data privacy and compliance.
Mining executives in global companies are raising questions about how to comply with fundamental security obligations depending on the geography they operate in.
“It is a challenge having security policies across multiple locations,” Campbell says. “When companies are geographically split you struggle for consistency and costs increase. Many companies will engage service providers to bridge that gap and rely on a partner to deliver outcomes they would struggle to deliver in-house.”
|
Mining companies not immune to emerging enterprise IT threats There are many technology applications specific to the mining industry’s processes. However, this does not mean that mining companies can afford to overlook general emerging security risks in the changing corporate IT space. The adoption of BYOD (bring your own device) and a greater use of smart devices in operational areas to access the cloud call for the same prudent approach to cyber security as a bank.
|
Modern defense involves people and technology
As devices become more connected and processes become more digitised, mining companies have to contend with more network-born security threats. Traditionally, mining has run on priority stand-alone systems. However, greater IT-OT integration and cyber security risk factors mean business leaders need to take a holistic view of their organisations, including any challenges arising from digital silos.
Technology alone cannot prevent every kind of cyber-attack, and industry leaders must understand the importance of staff skills as part of their broader security strategy.
Sixty-two per cent of organisations surveyed in the security report said they have too few experts available to implement their security strategies. In the Resources sector, security event analysis and corrective action were the security skills that were most lacking.
“There is a correlation between greater awareness at the board level and spending. Some 75 per cent of businesses surveyed plan to increase their security investment,” Campbell says. “However, the lack of skilled staff will continue to present a significant challenge for mining companies.”
"“More than one-third (34.3 per cent) of respondents across all industries cited a lack of security awareness training as very challenging,”
Source: Telstra Cyber Security Report 2016"
Alongside the need for tactical skills, companies must foster a culture of awareness throughout their organisations, not just at the board level. “The only way to solve these issues is with education. We always preach education – you can spend as much as you like on security, but if your employees aren’t aware of policies, the value of data, or threats, it will always be a challenge,” Campbell adds.
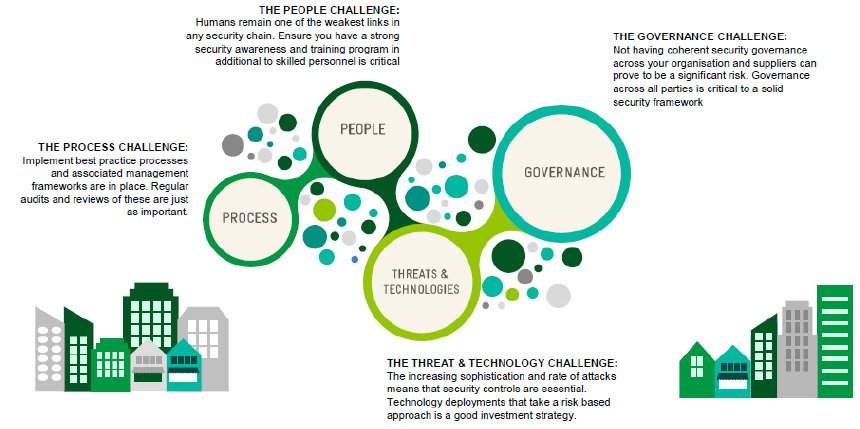
Business security fundamentals
There’s four core security fundamentals that should be addressed in your cyber security program. Do you have these covered?
|
Biggest cultural shift involves move to proactive security Many mining companies still see security as an afterthought, not a strategic enabler – particularly when commencing a new project or initiative. Telstra’s Hindes says miners need to embrace security as part of their day-to-day operations and prioritise what the security implications are of every initiative. Security needs to be seen as an enabler, not an inhibitor.
|
Hindes says that, while the percentage of breaches from internal staff is still at about 50 per cent, the industry needs to place a greater focus on security as a core specification and not an add-on.
“In the resources sector there are so many parties involved in the construction and operation of projects, and multiple companies in the supply chain. We are now seeing a lot more specifications regarding security obligations,” he says.
Today’s chief information security officers (CISOs) must adopt a multidisciplinary approach. As well as security expertise, they need to be well versed in corporate governance and risk management, while trying to maintain overall business objectives.
This cultural change is occurring at the highest levels of security strategy and those that conduct regular briefings with C-level or line of business managers are better equipped to handle security incidents, the Telstra report says.
It is now essential for C-suite members to fully understand how to integrate cyber security into their management processes.
Preparing from tomorrow's challenges
Rapid advances in mining technology mean IT and business leaders need to prepare for tomorrow’s cyber security challenges.
There are a number of IT and OT trends likely to challenge miners such as the rise of connected devices across the entire supply chain.
For example, the Internet of Things has enormous potential to benefit businesses. However, like all emerging technologies, IoT adoption needs to be managed proactively to reduce security risks. In the realm of corporate IT, mining companies are using more smart devices and cloud applications, which, like the IoT, improve business processes, but also require ongoing oversight.
Campbell says increased use of portable devices is likely to result in the propagation of malware from desktops to mobile phones and tablets, which can be encrypted by ransomware, causing sensitive data to be lost or stolen.
“On the cloud side there are many challenges. As organisations adopt software as a service (SaaS), IT departments will be less in control of the data they can inspect as staff use a range of applications,” he says. “The growing danger of shadow IT is that staff can share – not always maliciously – sensitive data and expose the organisation to liability and brand damage.”
Tomorrow’s cyber security strategies will also involve a shift of security controls and tool sets into the cloud where they can monitor what is being used outside the corporate boundary.
"“Security is not about preventing employees from using cloud and mobile apps, but you need to find a balance where you maintain visibility over how they are used.”
Neil Campbell, Director of Security, Telstra"
|
Working with partners to reduce risk Meeting the rising number of cyber security challenges may seem daunting for in-house IT departments with limited budgets and skillsets, but partnering can raise defensive capabilities. “Security knowledge is a rare resource – there aren’t enough of the ‘right people’ to go around so it is a matter of leveraging skills,” Campbell says.
|
Another important strategy for preparing for the future is training staff on the type of threats going around – both persistent and emerging.
“This is fundamental as you can never have enough training or awareness in your organisation, but it is not an easy thing to do. Some mining companies have initiated security academies and are running security-related education programs,” Campbell says.
"“The relationship between service providers and geographically split companies must be embedded in the organisation.”
Alan Hindes,
Global Industry Executive, Mining, Oil and Gas, Telstra"
|
Growing demand for Cyber insurance Companies are looking, although it’s early days, at taking up insurance to supplement what they do in-house if their defences fail, Campbell says.
|
Conclusion
Mining companies are going through a period of extensive technological change. At the same time, they have to deal with a growing number of cyber security threats as more processes go digital and more devices join their networks. More frequent cyber-attacks, combined with limited in-house skills are affecting their ability to mitigate these risks.
To take full advantage of new technologies and services, IT and business decision-makers must view security as an innovation enabler. Training, education and partnering with the right organisations are core components of a modern cyber security strategy in an increasingly global business arena.
Telstra can assist your organisation to meet your increasingly sophisticated security requirements.
For more information or to discuss the cyber health of your organisation, contact Telstra at: CyberSecurityConsulting@team.telstra.com

Author and bio

As the Global Industry Executive for the mining, oil and gas industry verticals, Alan’s role is focused on developing new markets, industry partnerships and joint ventures, as well as opportunities for new solutions and services for the resources sector.
Alan brings to this role depth of knowledge and rich expertise, from a career spanning over 45 years’ working in the telecommunications and technology sectors, predominantly at Telstra. Alan holds a Master of Business Administration, Graduate Diploma of Business and a Diploma of Electronic Engineering.
A career highlight was Alan’s time spent working in Vietnam as a Business Development Manager, where he negotiated a trial market agreement with the Vietnamese Government for the deployment of a mobile network.
Save
Save



























